|
Ontrack Content Security (CSP) security improvements
|
Ontrack security has been significantly enhanced by modifying the CSP (Content Security Policy) to block the execution of inline scripts. This change stops malicious scripts being injected into Ontrack pages, offering stronger protection against XSS (Cross-Site Scripting) attacks. Genuine EBS scripts are marked with a unique value to identify these as safe to run.
In order to facilitate the use of custom JavaScript by customers, scripts added in the following supported ways will also be considered authorised. It is therefore important to ensure that access to these locations is carefully controlled:
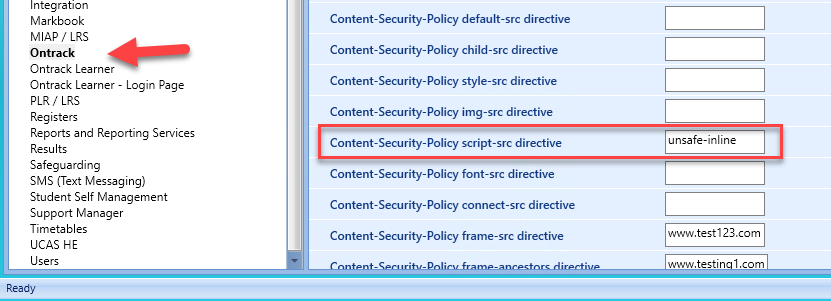
Should this security change cause unforeseen issues, Ontrack can be reverted to allow the use of inline scripts by adding the value unsafe-inline in the Content-Security-Policy > script-src directive institution setting.
Adding this attribute is not recommended and should only be considered as a short-term workaround.
Default directives such as those relating to the use of the Google translate widget, have been removed from the out-of-the-box CSP, following the security principle of least privilege. If these were in use, the functionality will be blocked on upgrade. If the functionality is still required, use the Dev Tools features found in Chrome and Edge to review any console errors relating to the CSP, and add any missing domains to the appropriate content security policy directive.
Two further new institution settings have been added to give greater control to institutions over the content and restrictions applied in the CSP:
|
Ontrack Institution Settings
|
|
Analytics snippet usage of head.cshtml to add in the <head> element
|
Google Tag Manager recommends that scripts are embedded in the <head> tag. To support this, the contents of a script named head.cshtml placed in the analytics folder will be included in the <head> tag of every page in Ontrack.
Files with any other name will continue to be included in the <body> tag of each page.
|
Configurable Functionality
|